[German] A security researcher with the alias @Sword_Sec, based in Turkey, has identified a potential security vulnerability in TeslaMate, an open-source application popular among Tesla enthusiasts for data logging (note: TeslaMate is independent of Tesla). The researcher, Seyfullah Kılıç, found that improperly configured TeslaMate servers, when exposed to the internet, could allow unauthorized access to sensitive data from hundreds of Tesla vehicles.
[German] A security researcher with the alias @Sword_Sec, based in Turkey, has identified a potential security vulnerability in TeslaMate, an open-source application popular among Tesla enthusiasts for data logging (note: TeslaMate is independent of Tesla). The researcher, Seyfullah Kılıç, found that improperly configured TeslaMate servers, when exposed to the internet, could allow unauthorized access to sensitive data from hundreds of Tesla vehicles.
In short: A tweet brought to my attention highlights Seyfullah Kılıç’s discovery of significant security risks within the TeslaMate application.
Further details are available in the article Türk güvenlik araştırmacısı, Tesla sahiplerinin kullandığı uygulamadaki açığı buldu. For those who read Turkish, the article elaborates on Seyfullah Kılıç’s findings regarding security vulnerabilities in the TeslaMate application.
TeslaMate is an open-source data logging tool that allows Tesla owners to self-host and visualize their vehicle’s data, including temperature, battery status, charging information, speed, and location data.
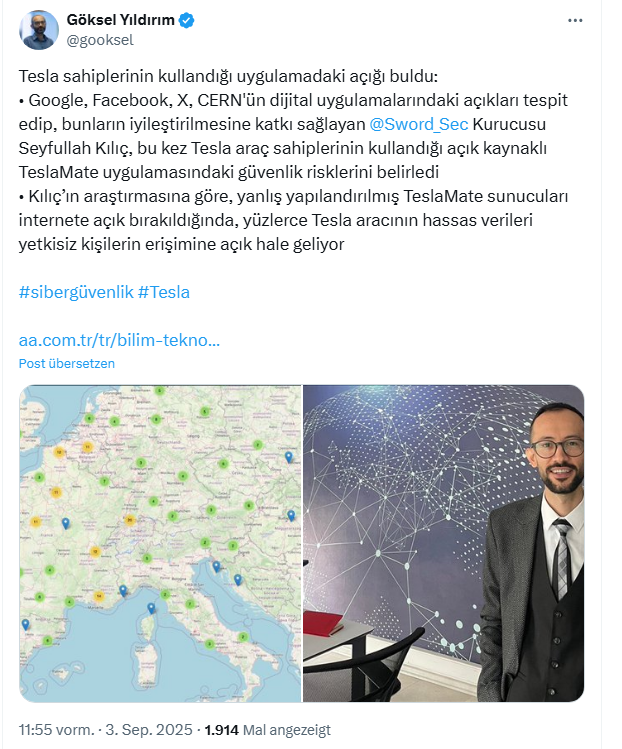
Kılıç’s research revealed that when TeslaMate servers are misconfigured and publicly accessible, sensitive information from numerous Tesla vehicles, such as location data, speeds, software versions, charging histories, and driving logs, could be exposed to unauthorized individuals.
To demonstrate the potential impact, Kılıç published the technical details of his findings and launched teslamap.io, a website visualizing the locations of the affected Tesla vehicles.
This discovery was also covered by TechCrunch in their article Security researcher maps hundreds of TeslaMate servers spilling Tesla vehicle data. Seyfullah Kılıç stated, “Our goal is not to exploit these vulnerabilities, but to raise awareness and ensure that people using open source software such as TeslaMate take security precautions. These risks can be avoided by simply verifying identities or configuring a firewall.”